Earth Ammit goes after drone companies
The threat cluster has targeted South Korea and Taiwan entities via the supply chain
A roundup of some of the noteworthy developments in the cybersecurity landscape, encompassing the latest vulnerability discoveries and emerging attack trends. Here are this edition’s top stories -
↘️ Vulnerabilities in Apple's AirPlay protocol and the accompanying software development kit (SDK) could allow attackers to take over devices, in some instances without user interaction, according to new findings from Oligo. The 23 vulnerabilities could be exploited to take over not just Apple devices but also third-party devices that use the AirPlay SDK. Some of the other impacts include adversary-in-the-middle (AitM) attacks, information disclosure, and denial-of-service (DoS). While issues can only be exploited by attackers on the same network, they allow taking over vulnerable devices and using the access as a launchpad to compromise other AirPlay-enabled devices on the same network. The issues, collectively named AirBorne, have since been addressed by Apple. [The Hacker News / WIRED]
↘️ A coalition of private sector companies and law enforcement agencies have taken down the infrastructure associated with Lumma Stealer and DanaBot. Charges have also been unsealed against 16 individuals for their alleged involvement in the development and deployment of DanaBot. The malware is equipped to siphon data from victim computers, hijack banking sessions, and steal device information. More uniquely, though, DanaBot has also been used for hacking campaigns that appear to be linked to Russian state-sponsored interests. All of that makes DanaBot a particularly clear example of how commodity malware has been repurposed by Russian state hackers for their own goals. In tandem, about 2,300 domains that acted as the command-and-control (C2) backbone for the Lumma information stealer have been seized, alongside taking down 300 servers and neutralizing 650 domains that were used to launch ransomware attacks. The actions against international cybercrime in the past few days constituted the latest phase of Operation Endgame. In a separate development, U.S. and Dutch law enforcement, with the help of Lumen researchers, have disrupted 5socks and Anyproxy, two proxy-for-rent services that were used by criminals for ad fraud and DDoS and brute-force attacks. [The Hacker News]

↘️ Several cybersecurity and intelligence agencies from Australia, Europe, and the United States issued a joint alert warning of a state-sponsored campaign orchestrated by the Russian state-sponsored threat actor APT28 targeting Western logistics entities and technology companies since 2022. “This cyber espionage-oriented campaign targeting logistics entities and technology companies uses a mix of previously disclosed TTPs and is likely connected to these actors’ wide scale targeting of IP cameras in Ukraine and bordering NATO nations,” the agencies said. The attacks are designed to steal sensitive information and maintain long-term persistence on compromised hosts. [The Hacker News]
↘️ The China-nexus cyber espionage group tracked as UNC5221 has been attributed to the exploitation of a pair of security flaws affecting Ivanti Endpoint Manager Mobile (EPMM) software (CVE-2025-4427 and CVE-2025-4428) to target a wide range of sectors across Europe, North America, and the Asia-Pacific region. The intrusions leverage the vulnerabilities to obtain a reverse shell and drop malicious payloads like KrustyLoader, which is known to deliver the Sliver command-and-control (C2) framework. “UNC5221 demonstrates a deep understanding of EPMM's internal architecture, repurposing legitimate system components for covert data exfiltration,” EclecticIQ said. “Given EPMM’s role in managing and pushing configurations to enterprise mobile devices, a successful exploitation could allow threat actors to remotely access, manipulate, or compromise thousands of managed devices across an organization.” [The Hacker News]
↘️ Microsoft revealed that a Türkiye-affiliated threat actor codenamed Marbled Dust exploited as zero-day a security flaw in an Indian enterprise communication platform called Output Messenger as part of a cyber espionage attack campaign since April 2024. The attacks, the company said, are associated with the Kurdish military operating in Iraq. The attacks exploited CVE-2025-27920, a directory traversal vulnerability affecting version 2.0.62 that allows remote attackers to access or execute arbitrary files. It was addressed in December 2024. [The Hacker News]
↘️ Cryptocurrency giant Coinbase disclosed that unknown cyber actors broke into its systems and stole account data for a small subset of its customers. The activity bribed its customer support agents based in India to obtain a list of customers, who were then approached as part of a social engineering attack to transfer their digital assets to a wallet under the threat actor’s control. The attackers also unsuccessfully attempted to extort the company for $20 million on May 11, 2025, by claiming to have information about certain customer accounts as well as internal documents. The compromised agents have since been terminated. While no passwords, private keys, or funds were exposed, the attackers made away with some amount of personal information, including names, addresses, phone numbers, email addresses, government ID images, and account balances. Coinbase did not disclose how many of its customers fell for the scam. Besides voluntarily reimbursing retail customers who were duped into sending cryptocurrency to scammers, Coinbase is offering a $20 million reward to anyone who can help identify and bring down the perpetrators of the cyber attack. [The Hacker News]
↘️ The threat actor known as Earth Ammit targeted a broader range of organizations than just Taiwanese drone manufacturers, as initially supposed. While the set of attacks was believed to be confined to drone manufacturers in Taiwan, a subsequent analysis has uncovered that the campaign is more broader and sustained in scope than previously thought, hitting the heavy industry, media, technology, software services, healthcare, satellite, and military-adjacent supply chains, and payment service providers in both South Korea and Taiwan. The attacks targeted software vendors and service providers as a way to reach their desired victims, who were the vendors’ downstream customers. [The Hacker News]
↘️ The Russia-linked threat actor referred to as COLDRIVER has been observed distributing a new malware called LOSTKEYS as part of an espionage-focused campaign using ClickFix-like social engineering lures. The attacks, detected in January, March, and April 2025, targeted current and former advisors to Western governments and militaries, as well as journalists, think tanks, and NGOs, as well as individuals connected to Ukraine. LOSTKEYS is designed to steal files from a hard-coded list of extensions and directories, along with sending system information and running processes to the attacker. [The Hacker News]
↘️ Israeli company NSO Group was ordered by a federal jury in the U.S. to pay Meta-owned WhatsApp WhatsApp approximately $168 million in monetary damages, more than four months after a federal judge ruled that the Israeli company violated U.S. laws by exploiting WhatsApp servers to deploy Pegasus spyware targeting more than 1,400 individuals globally. In addition, the jury determined that NSO Group must pay WhatsApp $444,719 in compensatory damages for the significant efforts WhatsApp engineers made to block the attack vectors. WhatsApp originally filed the lawsuit against NSO Group in 2019, accusing NSO Group of exploiting WhatsApp using a then-zero-day vulnerability in the messaging app to target journalists, human rights activists, and political dissidents. NSO Group said it will appeal the ruling. [The Hacker News]
↘️ The Iranian state-sponsored threat group tracked as Lemon Sandstorm targeted an unnamed critical national infrastructure (CNI) in the Middle East and maintained long-term access that lasted for nearly two years using custom backdoors like HanifNet, HXLibrary, and NeoExpressRAT. The activity, which lasted from at least May 2023 to February 2025, entailed “extensive espionage operations and suspected network prepositioning – a tactic often used to maintain persistent access for future strategic advantage,” according to Fortinet. [The Hacker News]
↘️ A recently disclosed critical security flaw impacting SAP NetWeaver is being exploited by multiple China-nexus nation-state actors tracked as UNC5221, UNC5174, and CL-STA-0048 to target critical infrastructure networks and drop various malicious payloads. Targets of the campaign include natural gas distribution networks, water and integrated waste management utilities in the United Kingdom, medical device manufacturing plants oil and gas exploration and production companies in the United States, and government ministries in Saudi Arabia that are responsible for investment strategy and financial regulation. [The Hacker News]
↘️ North Korea-linked threat actors behind the Contagious Interview have set up front companies named BlockNovas LLC, Angeloper Agency, and SoftGlide LLC as a way to distribute malware during the fake hiring process. The activity exemplifies the sophisticated social engineering tactics employed by North Korean threat actors to lure developers. The disclosure comes as Pyongyang hackers are increasingly leveraging artificial intelligence as part of the fraudulent IT worker scheme. At the heart of these operations lies a comprehensive suite of AI-enhanced tools that work in concert and are used to create synthetic personas in order to sustain the deception. The facilitators utilize unified messaging services that provide a way to manage multiple personas across various communication channels simultaneously. These services also incorporate AI-powered translation, transcription, and summarization capabilities to help the IT workers communicate with their prospective employers. [The Hacker News]
↘️ A Chinese-language market used crypto scammers and money launderers Haowang Guarantee (aka HuiOne Guarantee) has announced it’s shutting down its operations after Telegram banned thousands of accounts and usernames that served as the infrastructure for the sprawling marketplace of third-party vendors. Blockchain analytics firm Elliptic said it facilitated more than $27 billion in total transactions, making it by far the largest single black market operation in the internet’s history. A second Telegram-based market known as Xinbi Guarantee has also been found to offer a similar model of third-party transactions and had facilitated $8.4 billion in deals since 2022 that included not only money laundering for scammers, but also stolen data, harassment for hire, and apparent sex trafficking. The fact that such markets, and several more, are openly accessible on the clearnet, it goes without saying that the Chinese-language crypto crime economy has no signs of slowing any time soon. [WIRED / The Hacker News]
↘️ New research has demonstrated a new problem-space adversarial attack called EvadeDroid that’s designed to effectively evade black-box Android malware detectors in real-world scenarios. “EvadeDroid constructs a collection of problem-space transformations derived from benign donors that share opcode-level similarity with malware apps by leveraging an n-gram-based approach,“ researchers from Radboud University’s Digital Security Group and Ruhr University Bochum said. “These transformations are then used to morph malware instances into benign ones via an iterative and incremental manipulation strategy.” The study revealed that EvadeDroid can “effectively deceive diverse malware detectors that utilize different features with various feature types,” achieving evasion rates of 80%–95% against DREBIN, Sec-SVM, ADE-MA, MaMaDroid, and Opcode-SVM with only 1–9 queries. [ScienceDirect]
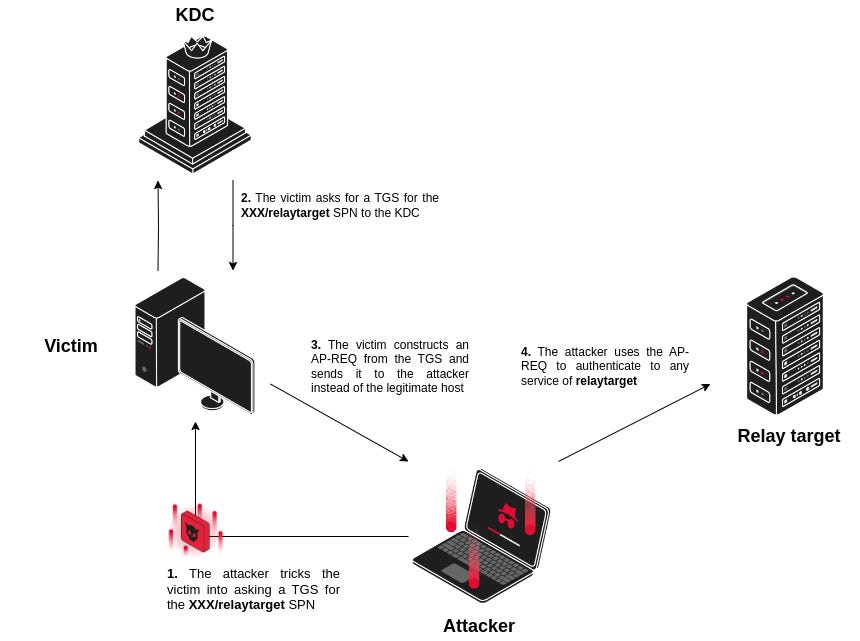
↘️ A novel attack method has been found to leverage multicast poisoning to execute pre-authenticated Kerberos relay attacks over HTTP using offensive tools like Responder and krbrelayx. While implementations of Kerberos relaying focused on DNS and SMB protocols, the new approach utilizes HTTP as a vector, exploiting the Link-Local Multicast Name Resolution (LLMNR) protocol to bypass security measures. “Such an alternative method has distinct prerequisites from the DNS/SMB ones and can be leveraged in specific cases where these two other vectors cannot be exploited,” Synacktiv said. “The main advantage of the presented relaying technique is that it can be potentially performed without authentication, via standard multicast poisoning. It can thus represent a viable alternative to Kerberos relaying over DNS when attack vectors such as mitm6 cannot be exploited.” Making matters worse, Synacktiv researchers found that it's possible to return “specific SMB error codes to make Windows SMB clients fall back to the WebDav HTTP client if the latter is available,” adding “this, as a result, allows triggering HTTP authentications from an SMB connection in a multicast poisoning context, opening the door to a more powerful relaying primitive.” [Synacktiv]
↘️ Cybersecurity researchers have shed light on the inner workings of hotkey-based keyloggers wherein threat actors could register custom hotkeys for any individual key (i.e., keyboard shortcuts for Windows to invoke specific functionality, such as “Alt + Tab” to switch between tasks). “A hotkey-based keylogger abuses this capability to capture the keystrokes entered by the user,” Elastic Security Labs said. “Not only alphanumeric and basic symbol keys, but also those keys when combined with the SHIFT modifier, can all be registered as hotkeys using the RegisterHotKey API. This means that a keylogger can effectively monitor every keystroke necessary to steal sensitive information.” To detect hotkey-based keyloggers, users are recommended to scan all HOT_KEY objects stored in ghpkHashTable to retrieve details about every registered hotkey. “If we find that every main key — for example, each individual alphanumeric key — is registered as a separate hotkey, that strongly indicates the presence of an active hotkey-based keylogger,” Elastic said. [Elastic]
↘️ Threat actors have been flagged using advanced obfuscation techniques like code virtualization, staged payload delivery, dynamic code loading to introduce new code at runtime via .NET reflection, Advanced Encryption Standard (AES) encryption, and creating multi-stage payloads that are self-contained within the original sample to evade sandbox detection and enable widespread distribution of malware families like Agent Tesla, XWorm, and FormBook/XLoader. [Palo Alto Networks Unit 42]
↘️ Cybersecurity researchers have detailed a new credential harvesting tool coined RemoteMonologue that weaponizes the Distributed Component Object Model (DCOM) to make object registry modifications and perform a session hijack by setting the RunAs value to “Interactive User.” Attackers can abuse COM object methods such as ServerDataCollectorSet, FileSystemImage, and UpdateSession to coerce remote NTLM authentications for password cracking and relay attacks. In a nutshell, each of these objects contains properties that can be manipulated to force the target system to attempt authentication against an attacker-controlled server. “RemoteMonologue provides the ability to target any of the three aforementioned DCOM objects (-dcom) to perform authentication coercion against a specified listener (-auth-to),” IBM researcher Andrew Oliveau said. “Additionally, it features a spraying module (-spray) to validate credentials across multiple systems, with the added benefit of capturing credentials. The tool also supports a NetNTLMv1 downgrade attack (-downgrade) and has an option to enable the WebClient service to facilitate HTTP authentications (-webclient).” [IBM X-Force]
↘️ A novel process injection technique dubbed Waiting Thread Hijacking (WTH) has been created as a “much stealthier version” of Thread Execution Hijacking. Developed by Check Point, the method employs waiting threads to execute code without triggering EDR alerts. While classic thread hijacking involves suspending a thread, modifying its context, and resuming it to execute malicious code, WTH targets threads that are already in a waiting state, such as those in Thread Pools, to overwrite the return address to redirect the execution flow to malicious code. [Check Point]
↘️ A new “cookie sandwich” technique can be used to bypass the HttpOnly flag on certain servers and steal cookies. “The cookie sandwich technique manipulates how web servers parse and handle cookies when special characters are used within them,” security researcher Zakhar Fedotkin said. “By cleverly placing quotes and legacy cookies, an attacker can cause the server to misinterpret the structure of the cookie header, potentially exposing HttpOnly cookies to client-side scripts. Because the Chrome browser doesn’t support legacy cookies, it lets attackers create a cookie name that starts with a $, like $Version, from JavaScript. Furthermore, quotes can be placed inside any cookie value.” [PortSwigger]
↘️ Cybersecurity researchers have disclosed an “impossible” XML External Entity (XXE) injection vulnerability in PHP that attackers can use to bypass multiple security mechanisms to access sensitive configuration files, private keys, and sidestep the authentication mechanism for SimpleSAMLphp (CVE-2024-52596). The shortcoming affects PHP applications using certain LIBXML flags during XML processing, potentially exposing critical server-side information even with security measures in place. The proof-of-concept, developed by Positive Technologies, uses tools like wrapwrap and lightyear to demonstrate the flaw with only LIBXML_DTDLOAD or LIBXML_DTDATTR flag set. [PT Swarm]