A roundup of some of the noteworthy developments in the cybersecurity landscape, encompassing the latest vulnerability discoveries and emerging attack trends. Here are this edition’s top stories -
↘️ The U.S. government has warned telecommunications companies and tech firms that undersea cables that ferry internet traffic across the Pacific Ocean could be vulnerable to tampering and espionage by Chinese repair ships. Specifically, concerns have been raised about a Chinese undersea cable maintenance company named SBSS, whose location-tracking beacons have been inoperative periodically over the past five years, according to radio and satellite data from commercial data provider MarineTraffic. [The Wall Street Journal]
↘️ Password manager service LastPass is warning of a malicious campaign targeting its users with the CryptoChameleon phishing kit that has been observed to target cryptocurrency platforms, government entities, and other services like Okta using spoofed sites. Victims are directed to fake websites (“help-lastpass[.]com”) via phishing emails, SMS messages, or even direct phone calls, tricking them into entering their account credentials. Threat actors then use the stolen data to sign in to the target’s LastPass account and change the phone number or email address to lock them out. The campaign is the latest to target LastPass, which said one of its employees was unsuccessfully targeted by a deepfake audio call impersonating the company’s CEO Karim Toubba. It also warned of another wide-scale phishing attack targeting its users last year, which included a link to a phishing page hosted on subdomains of “customer-lastpass[.]su.” [LastPass]

↘️ 49.6% of all internet traffic came from bots in 2023, a 2% increase over the previous year, with malicious automated traffic accounting for 32% of it. “The rise in popularity of Artificial Intelligence (AI) and Large Learning Models (LLMs) contributed to the increase in automated traffic in 2023,” Imperva said. The development comes as DNS-based DDoS attacks increased by 80% YoY and remain the most prominent attack vector as of Q1 2024. “DDoS attacks on Sweden surged by 466% after its acceptance to the NATO alliance, mirroring the pattern observed during Finland's NATO accession in 2023m,” Cloudflare said. It also follows a dramatic spike in cyberattacks and misinformation campaigns in the Philippines amid escalating geopolitical tensions with China, surging 325% compared to the same period last year. [Imperva / Cloudflare / Resecurity]
↘️ A critical security vulnerability (CVE-2024-2197, CVSS score: 9.1) could allow Chirp Access smart locks to be remotely unlocked. “Chirp Access improperly stores credentials within its source code, potentially exposing sensitive information to unauthorized access,” CISA said in an advisory. “Successful exploitation of this vulnerability could allow an attacker to take control and gain unrestricted physical access to systems using the affected product.” The flaw remains unpatched despite it being reported way back in March 2021. [Krebs On Security / CISA]
↘️ Open Web Advocacy (OWA) has raised concerns that in-app browsers “subvert user choice, stifle innovation, trap users into apps, break websites and enable applications to severely undermine user privacy,” adding they could be used by apps to inject arbitrary JavaScript via in-app browsers into third-party websites. [OWA]
↘️ A new report from Haaretz revealed that Israeli commercial spyware vendor Intellexa presented a proof-of-concept (PoC) system in 2022 called Aladdin that enabled the planting of phone spyware through online ads. Last year, the publication had disclosed that Insanet had developed a product called Sherlock that can infect devices via online advertisements to snoop on targets and collect sensitive data from Android, iOS, and Windows systems. To mitigate the attacks, it’s recommended that users install an ad blocker. The spyware threat has increased in recent years due to the companies uncovering new zero-click exploits to deliver such intrusive tools, even as tech giants like Apple have devised ways to reduce the attack surface. “The likelihood of a ‘mobile NotPetya’ event, characterized by a self-propagating mobile malware deliberately or accidentally spread through zero-click exploits, is increasing rapidly,” Recorded Future said. [Haaretz / Recorded Future]
↘️ Researchers have developed an exploit capable of unlocking all Saflok-brand RFID-based keycard locks which are used in hotels and properties. The attack entails using any keycard from the targeted property and extracting a certain code and then creating a pair of forged cards. The first custom card, when tapped against a Saflok lock, overwrites a crucial piece of its data, and then the second custom card can be used to unlock the door. [The Hacker News]
↘️ A fake e-shop scam campaign has been targeting Malaysia, Vietnam, and Myanmar since 2021 with phishing websites to distribute a malicious APK (Android application package) on social media platforms and WhatsApp, which siphons user credentials through SMS and can now also take screenshots and utilize accessibility services on the victim’s device, giving the attackers more control. [Cyble]
↘️ Law enforcement officials in 19 countries have shut down an online platform called LabHost that earned at least $1 million by selling phishing kits to cybercriminals, helping them launch attacks on thousands of individuals. LabHost was set up in 2021 to make it easier for hackers to create fake websites aimed at tricking people into revealing email addresses, passwords and bank details. Thirty-seven suspects were arrested, and more than 70 locations were searched in the U.K. and across the world. [The Hacker News]
↘️ Chinese and Russian hacking groups are increasingly shifting focus to edge devices — like VPN appliances, firewalls, routers and Internet of Things (IoT) tools — to conduct attacks owing to their nonexistent telemetry and the fact they lack support for EDR solutions. Attackers are also making a concerted effort to evade detection by using “living off the land,” or use of legitimate, pre-installed tools and software within an environment. The good news is that despite these efforts, companies are getting better about detecting compromises internally (up from 37% to 46% year-over-year), with global median dwell time in 2023 at 10 days, down from 16 days in 2022. [Google Cloud]
↘️ Indian government entities are at the receiving end of cyberattacks staged by Pakistan-linked actors such as Transparent Tribe and SideCopy, each of which has been observed delivering known remote access trojans like Crimson RAT and AllaKore RAT via spear-phishing campaigns. There is evidence to suggest that SideCopy operates under the umbrella of Transparent Tribe owing to infrastructure and tooling overlaps. [Seqrite]
↘️ Kremlin-controlled Sandworm, also called APT44, has established itself as Russia’s preeminent cyber sabotage unit, with the enduring threat hiding its attacks behind hacktivist personas such as XakNet Team, CyberArmyofRussia_Reborn (CARR), and Solntsepek. The formidable adversary, besides engaging in espionage, destructive, and influence campaigns targeting Ukraine, has been linked to widespread credential theft targeting global mail servers, aiming to maintain access to high-value networks that are of strategic political, economic, and military interest to Russia. The military intelligence unit’s favorite tactic for gaining initial access has been through exploitation of routers, VPNs, and other edge infrastructure, with follow-on activities leveraging legitimate tools and living-off-the-land techniques to evade detection. It’s also a sign of Sandworm shifting away from opportunistic disruptive operations it has carried out in the past to cyber espionage. [WIRED / Dark Reading / The Hacker News]
↘️ Google said investments in better security features, updated policies, advanced machine learning, application review processes, and developer onboarding helped in its battle against bad Android apps and actors trying to sneak into the Play Store. The company noted it blocked 2.28 million privacy-violating applications from being published and banned 333,000 accounts in 2023. [The Hacker News]
↘️ Hackers connected to the government of North Korea are exploiting lax DMARC email policies to send spoofed messages that allow them to pose as journalists or academics as part of phishing campaigns foreign policy experts. These highly targeted campaigns entail broad research and preparation to create tailored online personas, with the threat actors creating fake usernames and using legitimate domain names to impersonate individuals from trusted organizations. [The Hacker News]
↘️ Microsoft has previewed Zero Trust DNS (ZTDNS), which aims to allow an “administrator to lock down Windows outbound IP-based traffic to endpoints approved by a Protective DNS service.” [Microsoft]
↘️ Threat actors have been observed using compromised email accounts to send phishing emails containing links to PDF files hosted on Autodesk Drive. Recipients who attempt to view the document are taken to a phishing page and asked to provide their Microsoft account username and password. [Netcraft]
↘️ Law enforcement agencies from Australia, the U.K., and the U.S. revealed the identity of the kingpin behind the LockBit ransomware-as-a-service group as Dmitry Yuryevich Khoroshev, more than two months after a coordinated law operation felled the group’s dark web infrastructure. A 31-year-old Russian national, Khoroshev has been subjected to asset freezes, travel bans, and sanctions. However, he is unlikely face charges, given Russia’s policy against extraditing Russian nationals. LockBitSupp has since posted messages denying they are Khoroshev. [The Hacker News / Krebs on Security / CyberScoop / WIRED]
↘️ Various companies and state agencies in Indonesia such as the Indonesian National Police and the National Cyber and Crypto Agency have procured highly invasive spyware and other surveillance technologies from Israel, Greece, Singapore and Malaysia between 2017 and 2023, often via shadowy commercial networks that obscure the export of the surveillance technology to the country. This includes companies like Q Cyber Technologies (linked to NSO Group), the Intellexa consortium, Saito Tech (also known as Candiru), FinFisher and its wholly-owned subsidiary Raedarius M8 Sdn Bhd, and Wintego Systems. “Several of these imports have passed through intermediary companies located in Singapore, which appear to be brokers with a history of supplying surveillance technologies and/or spyware to state agencies in Indonesia,” Amnesty International said. It’s currently unclear who is being targeted, but the development is yet another sign that the unchecked spyware ecosystem continues to threaten citizens’ rights to privacy and free expression. Complicating matters further is the fact that Indonesia does not have laws specifically governing the lawful use of such tools. [Amnesty International]
↘️ Cybercriminals and advanced persistent threat (APT) actors alike have demonstrated an interest in compromised routers, surreptitiously coexisting inside the devices for use as an anonymization layer. [The Hacker News]
↘️ The U.K.’s contentious Investigatory Powers (Amendment) Bill (IPB) 2024 — called the snooper’s charter by critics — officially becomes a law, widening the digital surveillance powers wield by intelligence, law enforcement, and government agencies in the country. The goal, the government said, is to “guard against modern threats to national security” and better combat “evolving threats from terrorists, hostile state actors, child abusers and criminal gangs.” [GOV.UK]
↘️ More than 850,000 people in Europe and the U.S. have been allegedly duped into sharing card details and other sensitive personal information with a vast network of fake online designer shops apparently operated from the Fujian province in China. The sprawling criminal e-commerce network, codenamed BogusBazaar, has processed over a million orders with an aggregate order volume of $50 million over the past three years. Additionally, millions of stolen credit card details have been resold on dark web marketplaces, allowing other threat actors to purchase them and perform unauthorized online purchases. Launched with over 75,000 fake web shops since 2021, the campaign has diminished to 22,500 active sites. The organized e-crime group has also adopted an “infrastructure-as-a-service” model, where a core team is responsible for infrastructure management, while a decentralized network of franchisees operates the fraudulent shops. [SRLabs / The Guardian]
↘️ Patchwork (aka Dropping Elephant and Hangover), a threat actor believed to be of South Asian origin, has been observed leveraging a backdoor called Spyder in spear-phishing attacks targeting entities in Asia. Spyder is a variant of another backdoor called WarHawk that has been put to be use by the SideWinder group. Another hacking group called Careto (aka The Mask), has resurfaced after years to single out high-profile organizations in Latin America and Central Africa using complex implants such as FakeHMP, Careto2, and Goreto. The threat actor is believed to be active since at least 2007. [Kaspersky]
↘️ Nine security vulnerabilities uncovered in DJI Mavic 3 Series drones (CVE-2023-6948, CVE-2023-6949, CVE-2023-6950, CVE-2023-6951, CVE-2023-51452, CVE-2023-51453, CVE-2023-51454, CVE-2023-51455, and CVE-2023-51456) have the potential to facilitate unauthorized exfiltration of videos and pictures by exploiting the QuickTransfer Mode Wi-Fi protocol. [Nozomi Networks]
↘️ A newly discovered attack technique called TunnelVision (CVE-2024-3661) can be exploited to undermine VPN clients in that their traffic can be quietly routed away from their encrypted tunnels and intercepted by malicious actors on the same network, largely negating the whole purpose of VPNs. The attack plays out as follows: An attacker in a position to issue Dynamic Host Configuration Protocol (DHCP) leases to a target’s machine can use option 121 to force all data — even traffic that’s supposed to be destined for a VPN tunnel — through a gateway set up by the actor-controlled DHCP server [on the same network] and then eavesdrop on the traffic. [Krebs on Security / The Hacker News]
↘️ Apple’s decision to support alternative app stores from websites on iPhones in the E.U. region to comply with the Digital Markets Act (DMA) has opened up a new security loophole that leaves users of its Safari browser exposed to potential web activity tracking. The technique takes advantage of the MarketplaceKit API, which enables app marketplaces to install the apps they distribute to peoples’ devices. It’s made possible by the fact that both Safari and the MarketplaceKit process allow any website to make a call to the URI scheme of a particular marketplace. “As part of the installation flow, the MarketplaceKit process sends a unique client_id identifier to the marketplace backend,” Mysk said. “Multiple websites can trigger the MarketplaceKit process to send the same unique identifier client_id to the same marketplace backend. This way a malicious marketplace can track users across different websites.” Other security failings identified in the process could also open the door to various injection attacks. The development comes as it has emerged that Apple isn’t doing enough to make sure that apps from the likes of Meta and Spotify adhere to App Store rules that require iOS developers to provide reasons for using APIs that could be misused for fingerprinting purposes. [Mysk]
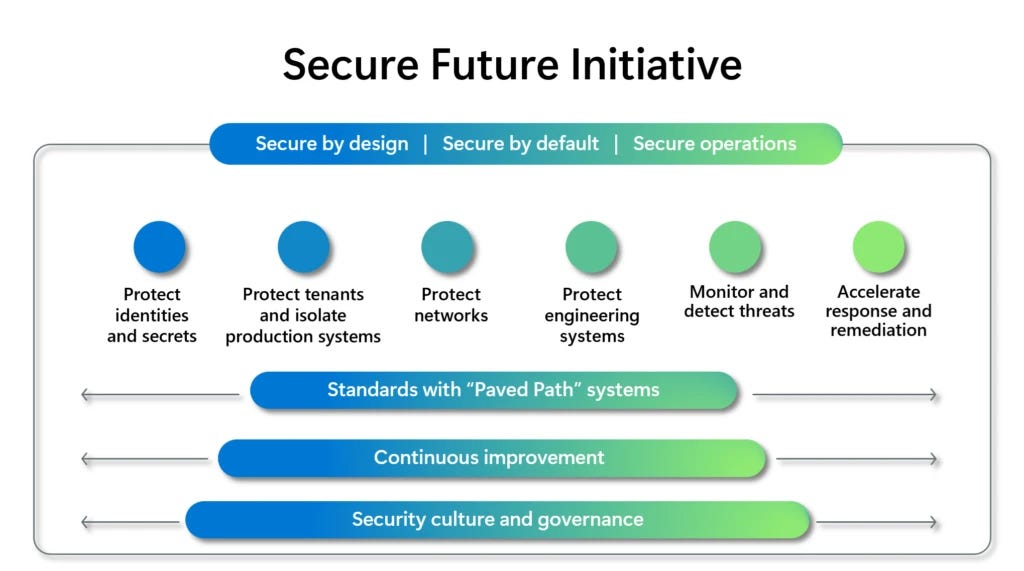
↘️ Microsoft is pledging significant reforms and a strategic shift to prioritize security above all other product features to overhaul and bolster security across its products and services. As part of its Secure Future Initiative (SFI), “we will instill accountability by basing part of the compensation of the company’s Senior Leadership Team on our progress in meeting our security plans and milestones,” the company said. The development comes in the aftermath of a scathing report that castigated the company for a series of security lapses that led to a breach of its infrastructure by a China-based nation-state group called Storm-0558 last year. [Microsoft]
↘️ The three individuals who solved the Zodiac Killer’s 340-character cipher (Z340) in December 2020 — David Oranchak, Sam Blake, and Jarl Van Eycke — released more details on the effort that went behind into cracking it after 51 years. “The first Zodiac cipher was solved within a week of its publication, while the second cipher was solved by the authors after 51 years, when it was discovered to be a transposition and homophonic substitution cipher with unusual qualities,” the authors said in a new paper. Its message began, “I hope you are having lots of fun in trying to catch me.” The unidentified Zodiac Killer is known to have murdered at least five people in the San Francisco Bay Area between December 1968 and October 1969. [arXiv / Popular Science / Wolfram / IEEE]