WhatsApp, Twitter, Signal, and other social media apps are set to face tougher rules in India.
The new regulations announced by the country’s Ministry of Electronics and Information Technology (MeitY) require that social media companies acknowledge complaints within 24 hours and resolve them within 15 days. Services must also remove nudity and sexually explicit content within 24 hours of flagging such posts.
Also included is an obligation that’s likely to once again put “significant” messaging-focused apps in a spot and threaten the core of how they function.
It mandates such services to identify the “first originator” of a message to allow “prevention, detection, investigation, prosecution or punishment of an offence related to sovereignty and integrity of India, the security of the State, friendly relations with foreign States, or public order.”
In other words, if any problematic content has been passed around on messaging apps, the government wants to be able to track down the original sender who instigated it.

“This first originator is not about the content, it's about who began the instigation,” said India’s IT minister Ravi Shankar Prasad. “If it started outside of India, they will have to track down who started the mischief within India.”
Murmurs about the Indian government’s plans to enforce a traceability clause had been going the rounds since July 2019, when it asked WhatsApp to identify the sources of anonymous rumors that led to lynchings and violence in the country.
But the Facebook-owned instant messaging app has argued this would compromise its end-to-end encryption.
WhatsApp has 530 million active users in India.
The catch here is that it’s impossible to identify who the instigator of a particular incident is without looking at the content, which would also mean circumventing encryption barriers to access the messages.
At the same time, it’s worth pointing out that if the identity of the individual sending the objectionable message is already visible to the platform as part of its data collection practices, then it’s possible such data can be shared without breaking encryption.
India’s Internet Freedom Foundation slammed the proposed draft rules, stating it would undermine the privacy of users, and that it “would be a tremendous expansion in the power of the government over ordinary citizens eerily reminiscent of China’s blocking and breaking of user encryption to surveil its citizens.”
What’s trending in Security?
🇷🇺 As the investigation into the SolarWinds hack continues, White House official Anne Neuberger, who is leading the government’s response to the espionage campaign, said the attack was executed from within the U.S. despite its alleged Russian origins.
Security researchers speaking to The Wall Street Journal also disclosed that hackers used Amazon's cloud-computing data centers to launch a key part of the attack. "Amazon has shared this information privately with the U.S. government, but unlike other technology companies, it has balked at making it public," according to the report. [Bloomberg / The Wall Street Journal]
🔍 The Intercept obtained a massive police database, developed by private defense company Landasoft, used by the Chinese government to facilitate police surveillance of citizens in Xinjiang, home to millions of oppressed Uyghur Muslims.
What's more, the publication also found that enterprise giant Oracle marketed its own analytics software to enable Chinese police "do criminal analysis and prediction." Oracle said the materials showed "what our products could do if others built on top of them" and were "aspirational business development ideas" that "do not indicate any targeted or intended sales/support execution," and that it's not selling data analytics software "for any of the end uses implied in the materials." [The Intercept]
🇰🇵 The U.S. Justice Department indicted three suspected North Korean hackers for allegedly conspiring to steal and extort over $1.3 billion in cash and cryptocurrencies from financial institutions and businesses. [The Hacker News]
🇨🇳 New research by Check Point found that a Chinese threat actor dubbed APT31 had access to a U.S. hacking tool years before it was leaked by the Shadow Brokers in 2017. [The Hacker News]

⚠️ Speaking of supply chain attacks, security researcher Alex Birsan disclosed a novel technique called "dependency confusion" or a "substitution attack" that he leveraged to break into dozens of high-profile companies.
The exploit takes advantage of a relatively simple trick: replacing private packages with public ones. This is achieved by uploading counterfeit projects using the same names to open source repositories including PyPI, npm, and RubyGems, which are then automatically distributed downstream into the various companies' internal applications without the need for social engineering lures or trojans. [The Hacker News]
🤖 A botnet used for illicit cryptocurrency mining activities has been found to abuse Bitcoin (BTC) transactions to camouflage command-and-control IP addresses via the blockchain and stay under the radar. Tracked under the moniker "SkidMap," researchers cautioned the technique, if more broadly adopted, could make botnet takedowns much harder to accomplish. [Akamai / Ars Technica]
🚨 New research has found that it's possible to abuse website favicons as "supercookies" to track you across incognito windows, VPNs, and Pi-holes. [Motherboard]
🔈 After TikTok, it's now the turn of Clubhouse to face the heat for its security stumbles. Besides inviting scrutiny for its aggressive collection of users' contact lists and lack of end-to-end encryption, the popular audio chatroom app said it's putting new safeguards in place after an unidentified user streamed audio feeds from "multiple rooms" into a third-party website. "Users of the invitation-only iOS app should assume all conversations are being recorded," Stanford Internet Observatory said. [Bloomberg / WIRED]
🇺🇦 The operators of Egregor ransomware were arrested in Ukraine as a result of a joint investigation between French and Ukrainian police. But the setback is only expected to be temporary. [Dark Reading]
🕸️ Brave fixed a bug in the Tor node bundled with the browser that sent queries for .onion domains to public internet DNS resolvers rather than Tor nodes. [The Hacker News]
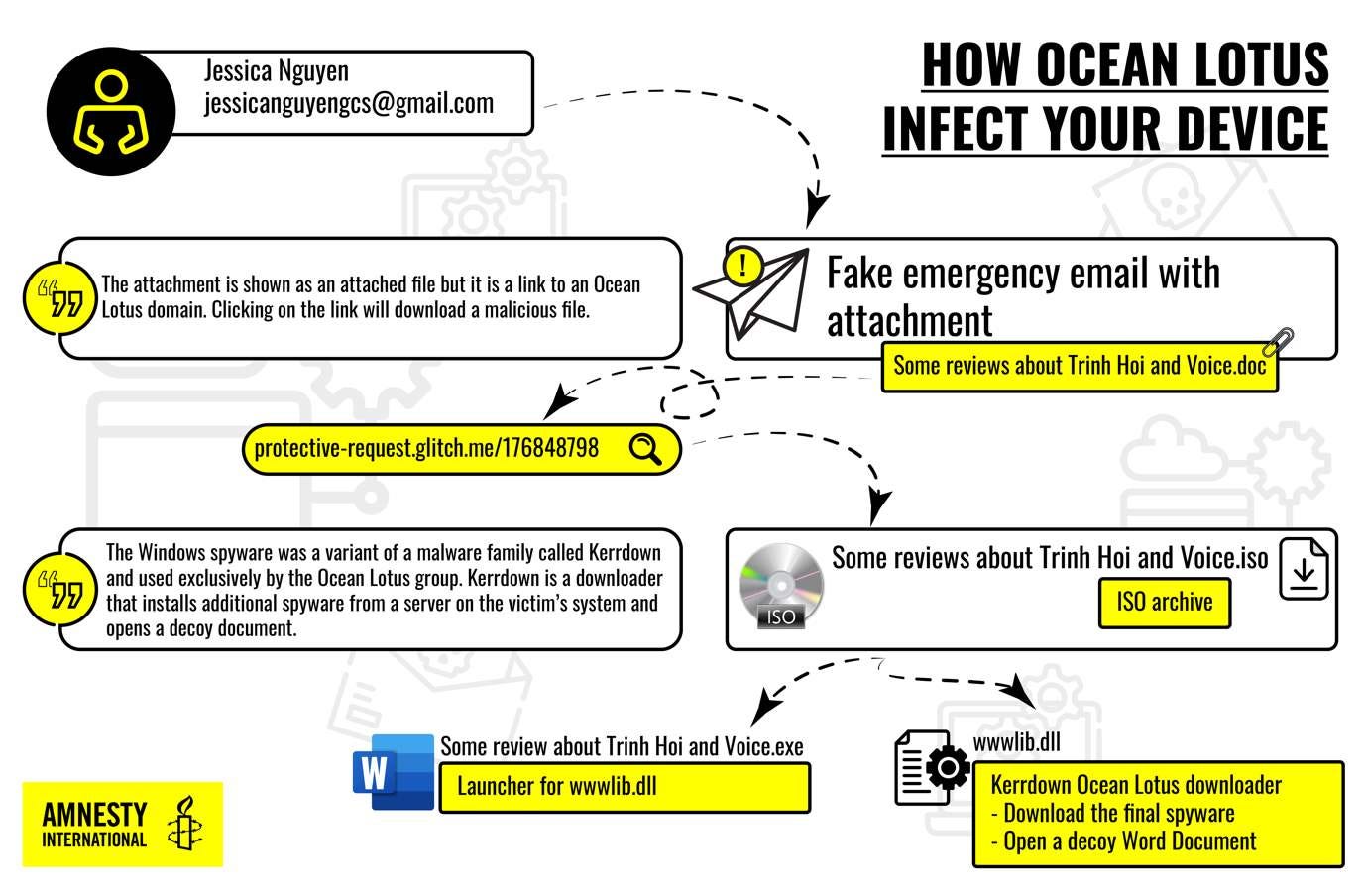
🇻🇳 Vietnam now joins the ranks of governments using spyware to crack down on human-rights defenders. The attacks were traced to a group called Ocean Lotus. [Amnesty International]
🌐 Tracker blocking measures incorporated by browser makers and the ad tech industry’s attempts to find sneaky ways to keep surveilling web users has always been a never-ending arms race. But a new study shows that marketers are increasingly adopting a technique called CNAME cloaking to get around such defenses. [The Hacker News]
🛡️ Researchers say a change in iOS 14.5 beta, which improves how iOS handles pointers, makes sandbox escapes and "0-click" attacks much harder to pull off. Also coming to iOS 14.5 is a feature that will redirect all fraudulent website checks through its own proxy servers as a workaround to preserve user privacy and prevent leaking IP addresses to Google. [Motherboard / The Hacker News]
💻 Threat actors are beginning to adapt malware to target the Apple's latest generation of Macs powered by its new Arm-based M1 silicon. [The Hacker News]
🔐 A security researcher is recommending against LastPass password manager after detailing seven trackers found in the Android app. LastPass said it can be turned off in settings. [The Register]
📺 YouTube took down 2,946 channels and accounts since the start of the year that were part of Chinese state coordinated influence operation. [Google Threat Analysis Group]
🗣️ Researchers have uncovered gaps in Amazon's skill vetting process for the Alexa voice assistant ecosystem that could allow a malicious actor to publish a deceptive skill under any arbitrary developer name and even make backend code changes after approval to trick users into giving up sensitive information. [The Hacker News]
📧 A previously unknown group called LazyScripter has been observed leveraging phishing campaigns to target the airlines sector with remote access trojans such as Octopus and Koadic. [Malwarebytes]
🗃 The past fortnight in data breaches, leaks, and ransomware: Adorcam, Bombardier, Oxford University's Division of Structural Biology, Fugro, Jones Day, Kroger, NurseryCam, SingTel, TietoEVRY, Transport for New South Wales, personal information of 102 million Brazilian citizens, and immigration records and COVID-19 test results of Jamaican travelers.
768%
That’s the percentage increase in Remote Desktop Protocol (RDP) attacks over the course of 2020. According to researchers at cybersecurity company ESET, 29 billion RDP attacks were detected over the year, as cybercriminals attempted to exploit remote workers.
That’s it for now. See you all in a week. Stay safe!
-Ravie



