Interactive livestreaming platform Twitch acknowledged a “breach” after an anonymous poster on the 4chan messaging board leaked its entire source code along with hundreds of gigabytes of sensitive company data, including a cache of internal tools, software development kits, and details about payouts to top streamers.

The Amazon-owned service said the data was exposed “due to an error in a Twitch server configuration change that was subsequently accessed by a malicious third party.” As a precautionary measure, the company has also reset all stream keys, requiring streamers to “manually update your software with this new key to start your next stream.”
What’s trending in security?
🇹🇬 A new report from Amnesty International links an Indian cybersecurity firm called Innefu Labs to spyware used to target an unidentified “prominent human rights defender” in Togo. [Amnesty]
⚠️ A group called BladeHawk has been targeting the Kurdish ethic group for more than a year through an Facebook-based spyware campaign that disguises backdoors in legitimate Android apps. More than 1,400 people are said to have downloaded the malicious app. [The Hacker News]
🇪🇺 The European Union officially linked Russia to a hacking operation known as Ghostwriter that targets high-profile EU officials, journalists, and the general public. "These malicious cyber activities are targeting numerous members of Parliaments, government officials, politicians, and members of the press and civil society in the EU by accessing computer systems and personal accounts and stealing data," the European Council said. [European Council]
🔢 Hackers stole cryptocurrencies from at least 6,000 customers of Coinbase by exploiting a flaw in its SMS-based two-factor authentication system. The intrusions took place earlier this year, between March and May.
In a similar development, cyber criminals are using Telegram bots to steal one-time password tokens (OTPs) and defraud people through banks and online payment systems, including PayPal, Apple Pay and Google Pay. [Bleeping Computer / Krebs On Security]
🇦🇪 Three former U.S. intelligence operatives are facing federal charges after allegedly having worked as cyber-mercenaries for the U.A.E. Part of the services provided by the Americans was the development of two “zero-click” exploit attacks — sophisticated cyber-intrusion techniques that can compromise security flaws implicit in popular mobile operating systems. [The Hacker News]
📅 2021 has had the highest number of zero-day exploits on record. “At least 66 zero-days have been found in use this year, according to databases such as the 0-day tracking project — almost double the total for 2020, and more than in any other year on record,” according to a new report. [MIT Technology Review]
🔝 Non-profit foundation Open Web Application Security Project (OWASP) has released an updated draft of its ranking of the top 10 vulnerabilities, the first changes to the list since November 2017. [OWASP]
💲 The operators of REvil ransomware made a surprise return two months after the group’s attacks on Kaseya in July 4. The group’s dark web infrastructure, which went down following the incident and raised speculations that may have shut shop, have all resurfaced back online.
Meanwhile, the Washington Post reported that the FBI refrained from sharing a ransomware decryptor with victims of the Kaseya ransomware attack for almost three weeks, as it carried out an operation to disrupt the REvil gang. "The key was obtained through access to the servers of the Russia-based criminal gang behind the July attack," the report said. But the planned operation never took off because mid-July REvil's dark web infrastructure went offline even before the FBI had a chance to execute its plan. [The Hacker News / The Washington Post]
📱 A new Android malware has been discovered spreading via text messages containing COVID-19 and electricity-themed lures with an aim to trick recipients into clicking a malicious link and allow cyber criminals to gain full control of the devices to steal personal and financial information. The malware has been dubbed TangleBot. [The Hacker News]
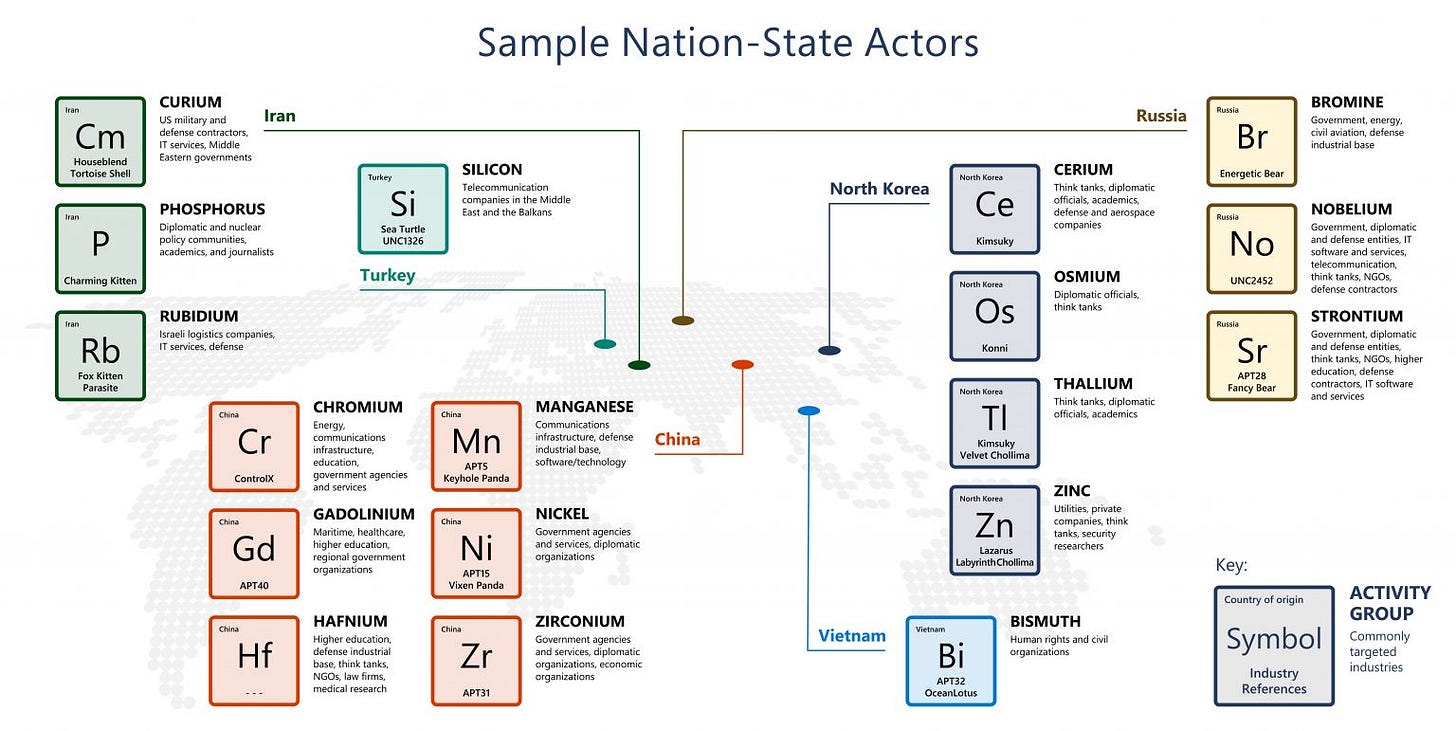
💥 Russia is the source of the lion’s share of nation-state cyber attacks between July 2020 and June 2021 (58%) primarily targeting government agencies for intelligence gathering, followed by North Korea (23%), Iran (11%), China (8%), and South Korea, Vietnam, and Turkey all with less than 1% representation, based on new data gathered by Microsoft. “The devastating effectiveness of the long-undetected SolarWinds hack also boosted Russian state-backed hackers’ success rate to 32% in the year ending June 30, compared with 21% in the preceding 12 months,” the Associated Press reported. [Microsoft]
🏫 Ransomware has been a hot-button topic in 2021 due to its impact on critical infrastructure, hospitals, and educational sectors. A new investigation by NBC News revealed how personal information of children are being leaked by ransomware gangs. Data from more than 1,200 American K-12 schools have been published in 2021 alone to date. [NBC News]
📶 Security consultant and penetration tester Bobby Rauch discovered that Apple’s AirTags — tracking devices which can be affixed to items like laptops, phones, or car keys — don’t sanitize user input, specifically, the phone number field AirTag owners use to identify their lost devices. This stored XSS flaw would allow an attacker to seed "weaponised AirTags" for harvesting the iCloud credentials of anyone who find them. [Bobbyr / Krebs On Security]
🤖 A new botnet called Mēris has been found to derive its power from tens of thousands of compromised devices that researchers believe to be primarily powerful networking equipment from MikroTik. The botnet — which has enslaved 250,000 devices into its mesh — has also been behind an assault on Russian internet giant Yandex's servers, making it the largest distributed denial-of-service (DDoS) attack recorded to date. Following the development, Russian telecom giant Rostelecom said it sinkholed part of the DDoS botnet. [The Hacker News / The Record]
🇷🇺 A Russian man, identified as Mr. A, was arrested at the Seoul international airport on accusations of developing code for the TrickBot malware gang, marking the second time an individual associated with the group has put behind bars. In June 2021, The U.S. Department of Justice arraigned in court a 55-year-old Latvian woman named Alla Witte for her involvement with the Trickbot malware gang since the group formed in November 2015. [The Record]
🇺🇦 The U.S. Department of Justice (DoJ) announced the extradition of Ukrainian national Glib Oleksandr Ivanov-Tolpintsev from Poland on charges of selling access to compromised computer systems via a specialized marketplace on the dark web.
Ivanov-Tolpintsev is suspected of being the operator of a botnet that was able to enslave devices infected with malware and automatically perform brute-force attacks against other internet-facing systems. Cyberscoop reported that investigators were able to track him down with the help of an email address used by the suspect to purchase vape products. [DoJ / CyberScoop]
⁉️ GitHub disclosed several high-severity vulnerabilities in npm packages, "tar" and "@npmcli/arborist," that could be used to achieve arbitrary code execution on Windows and Linux systems. The tar package receives 20 million weekly downloads on average, whereas arborist gets downloaded over 300,000 times every week. [Bleeping Computer]
🚨 Apple issued software updates to address a new vulnerability that allowed bad actors to target's iPhone via iMessage using an exploit called “FORCEDENTRY” that was abused to deploy Israeli company NSO Group’s Pegasus spyware tool. FORCEDENTRY is also a zero-click exploit that can be triggered without the user needing to click on a malicious link.
NSO develops and sells its exploits to government around the world as off-the-shelf software often for unlawful surveillance, and in July was linked to a campaign that involved breaking into iPhones belonging to dozens of journalists, human rights activists and politicians, according to an investigation by a consortium of newspapers. [The Hacker News]
🇨🇳 A network of fake social-media accounts linked to the Chinese government has attempted to draw Americans out to real-world protests against allegations that China engineered the virus that caused the COVID-19 pandemic. The campaign, noted for its rapid increase in size and “multiple shifts in tactics,” is also a troubling development, as it’s characterized by a “direct call for physical mobilization.” [FireEye]
📧 ProtonMail, the encrypted email service that’s built a reputation for safeguarding user data, said it had no choice but to provide IP address and other metadata about a climate activist to French authorities following a Swiss court order, leading to the individual's arrest. The company has since updated its privacy policy to spell out that it can be legally compelled to log IP addresses as part of Swiss criminal investigations. [The Hacker News]
🇦🇺 Encrypted phone firm Ciphr, which is popular among organized criminals, has announced plans to cease operations in Australia in what’s seen as a shakeup of the industry in the wake of disclosures that law enforcement agencies ran its own secure phone company called An0m to intercept messages exchanged between criminal gang members globally. [Motherboard]
ℹ️ The list of data breaches, leaks, and ransomware: Indonesia’s Badan Intelijen Negara, BrewDog, South Africa’s Department of Justice and Constitutional Development, Epik, Fimmick, Fortinet, GiantPay, Howard University, Iowa Farmers Cooperative, LinkedIn, MyRepublic Singapore, Neiman Marcus, Olympus, Portpass, Puma, Syniverse, The Telegraph, TTEC, The United Nations, Walgreens, Weir Group, and personal info of 106 million international visitors to Thailand.
Tips, Comments, Ideas?
Send them my way by writing replying to this email.
Thanks again for reading. See you in the next edition!